As a tech student in 2020 and beyond, you’ll want to understand a variety of different technologies, both old and new. You never know whether your workplace will be operating on a hodge-podge of 90s tech mixed with cloud applications, or a freshly-developed blockchain application unique to them.
Basing technology on the blockchain is a new and emerging trend, and it’s a technology you may want to learn if it’s something that interests you. In particular, if you’re looking to become a cybersecurity expert, you’ll want to understand both how the blockchain works, and how attacks against it function.
What Makes Blockchain Secure
So what makes blockchain technology so secure in the first place? The technology is designed with security in mind, and a lot of features are relevant to the security discussion.
First of all, you have the core concept of how a blockchain system functions. It is, literally, a chain of “blocks”, where each block is a piece of data that has been cryptographically hashed. Each block of data is a piece of information. In currencies, as a common and elementary example, each block is a transaction. When a user wants to make a transaction, their information is checked against the entire blockchain, to verify that the user indeed has currency available to spend. Once verified, their transaction is sent to miners, who compete to hash the data appropriately and add it to the chain.
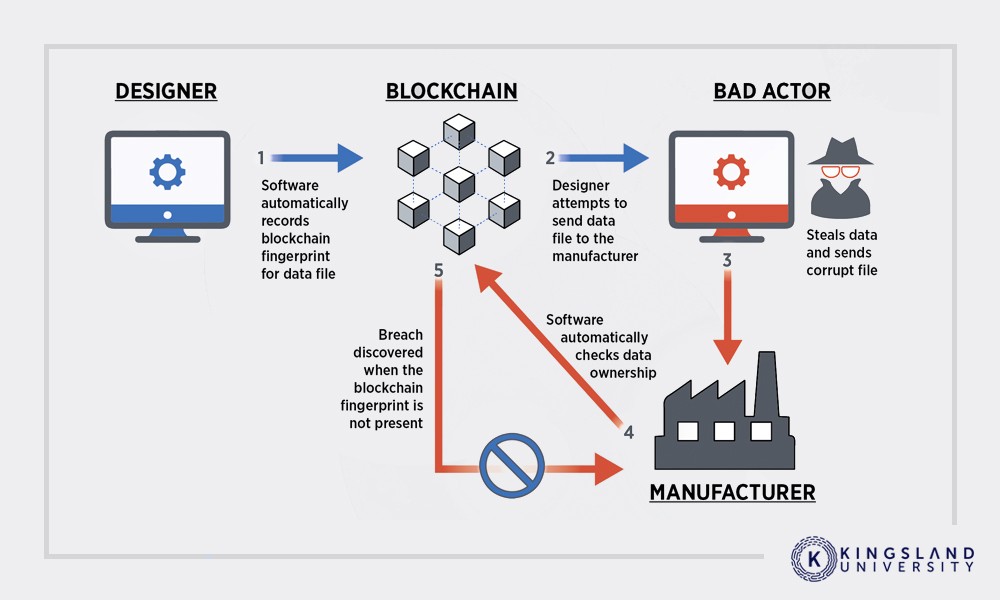
In manufacturing, blockchain technology may be used to secure sensitive files. If an attacker attempts to intercept those files and manipulate them, the blockchain fingerprint will be missing and those files will be rejected by the blockchain.
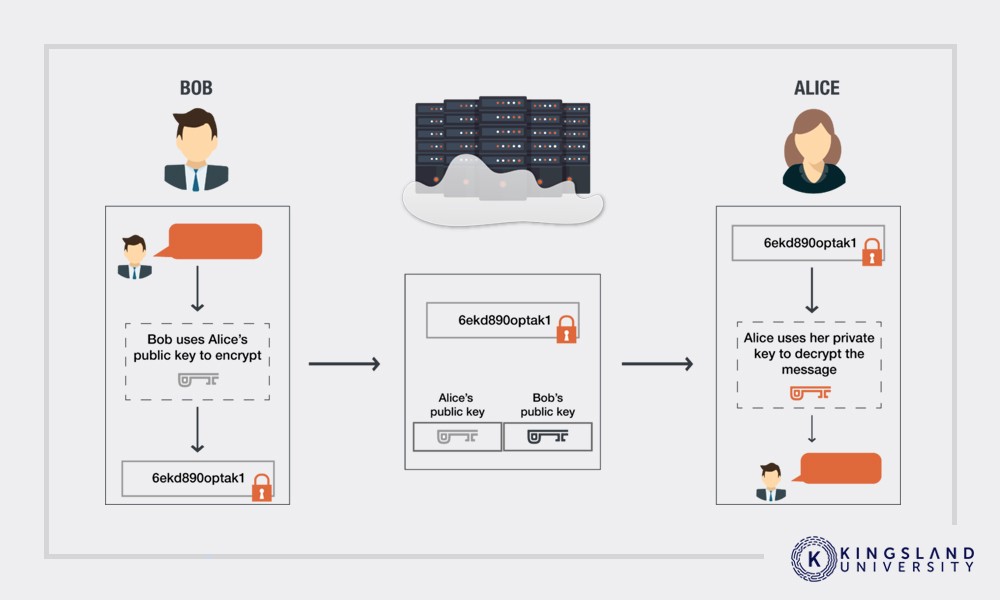
That cryptography is one part of the equation of security. The cryptography used in a blockchain may vary, but modern cryptography is generally quite difficult to crack without compromising the keys. When learning about blockchain technology, you’ll learn all about how cryptography functions and its purpose.
Additionally, the blockchain itself is a stored ledger of all of the data hashed into it. It’s a perfect, immutable transaction history that covers everything from the first action to the most recent action. More importantly, this ledger is not stored in one central location. Instead, it’s distributed between everyone who uses the technology. No one can manipulate this ledger, because they would need to manipulate every instance of it to make them match. This is the consensus protocol.
Different blockchain technologies work in different ways specifically, but they all share core elements relating to consensus and the chain of blocks, where individuals block each contains information about itself and the previous block, continuing a chain indefinitely.
While security seems immutable, humans are clever creatures, and there have already been a variety of different attacks on blockchain technologies, both actual and theoretical.
Blockchain technology is relatively new and complex, and that means there are a lot of people looking at a lot of different angles to figure out how to compromise it. Wherever there’s a potential profit motivation, there will be malicious actors. Indeed, blockchain tech has a lot of potential and actual vulnerabilities, that you will need to be aware of if you’re interested in modern cybersecurity.
Blockchain Technology Requires Proper Implementation of High-Quality Cryptography
Using high-end cryptographic processes to encode and hash data into a blockchain is great – if they’re implemented properly. It’s easy to treat these technologies as puzzle pieces that fit together, but using them in the wrong way can leave holes that can be exploited.
racking the cryptography directly may be rare, but cracking the way it’s put together is a lot easier. Not to mention the possibility of backdoors in the encryption allowing unsavory access.
Blockchain Technology Interfaces with Less Secure Technology
Blockchain technology itself might be securely designed, but it has to interface with other technology to be useful, and that point of contact can be exploited. There have been dozens of small and large-scale attacks on blockchain systems. Though blockchain extends well beyond cryptocurrency, coin exchanges have been major targets of sophisticated attacks. Attackers don’t have to necessarily compromise the protocol itself when they can simply hack an exchange that has failed to take proper security measures on their servers.
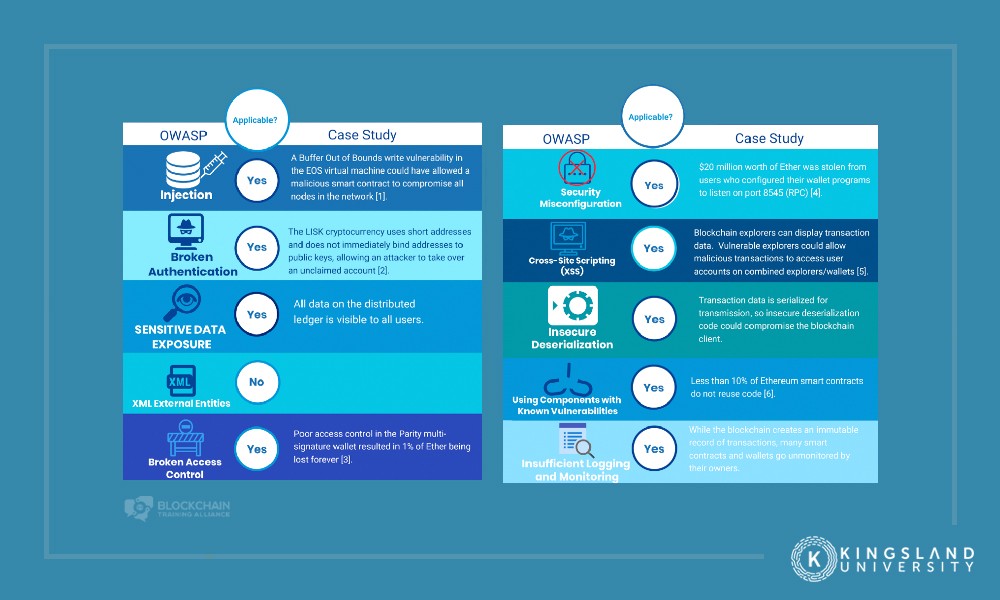
Looking for these vulnerabilities can be a golden opportunity for malicious actors, but it’s also proven to be lucrative for white hat hackers who chase bugs for bounties. These bug hunters have identified dozens of problems with various blockchain platforms.
One such attack targeted the “smart contract” system used by several digital currencies. In particular, it targeted Ethereum’s blockchain via the exchange Coincheck in Japan. The attack stole around 80 million dollars worth of ether from the exchange.
Blockchain’s Permanence for Currencies
Blockchain currency benefits are detriments as well. We’ve all read stories of people losing access to hugely valuable digital wallets, what was pocket change years ago became millions and was lost. The anonymity and security of the currency are both seen as a benefit, but for those who find themselves unable to recover a lost wallet, it’s a painful reminder that the technology requires security on both sides of the digital coin.
This is also an issue with the inability to insure or refund a transaction. With traditional currency, if some money is stolen from a bank account, a charge-back can rectify the situation and the insured bank takes the hit and is reimbursed. With something like cryptocurrency, if your currency is stolen from a wallet, it’s gone. The transaction cannot be reversed and is not insured.
In some cases, this can be rectified with something called a Hard Fork. A hard fork is a forced update to the entire blockchain that “forks” the chain before the theft, rewriting history to look like the theft never happened. The fork where it happened is abandoned, and the new fork becomes reality. Of course, this has its own set of problems; it requires a return to a central authority that can make such decisions, which is then open to further vulnerability.
Now, perhaps future iterations of a digital blockchain currency will integrate solutions to this problem, and perhaps that will make other attack vectors appear. The ever-evolving world of blockchain security is what you’ll learn when you study the subject.
Consensus Protocols
The distributed nature of the blockchain and the fact that the network requires consensus, and thus eliminates simple attempts at manipulation, also opens the technology up to broader forms of manipulation.
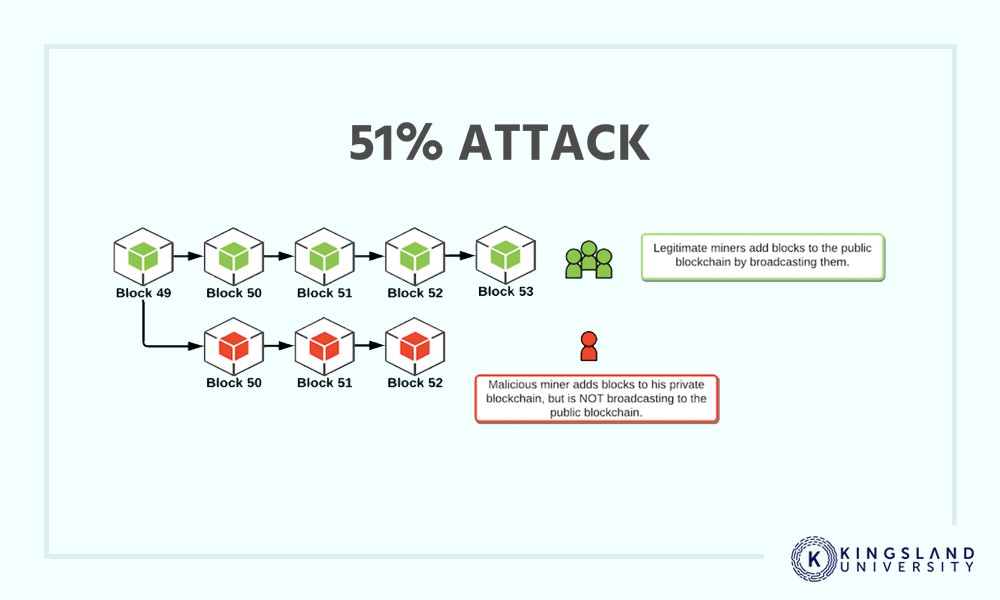
One speculated issue with blockchain is a majority problem. For example, with cryptocurrencies, a distributed network of miners is required to keep consensus. To change the “history” of a blockchain, an attacker would need to convince the consensus that their reality was the correct one. Normally, this would be impossible.
However, as more and more mining moves to Chinese warehouse farms and away from the distributed hands of people around the world, it becomes easier for a central group to dominate all mining, and thus, the consensus. In other words, one entity with sufficient computing power to throw at the task can take over a network and essentially write reality to be whatever they want it to be.
Called a 51% attack, when an attacker gains a majority control over the nodes in the network, they can control the new reality of the blockchain. While larger blockchains may or may not be at that point, several smaller networks have experienced these attacks already. The proof of concept has been proven, and now it’s a problem that must be solved.
Another attack, known as an “eclipse attack”, involves taking over communications to and from a node. By isolating a node and controlling traffic to it, an attacker can trick that node into wasting time and resources with false data, and thus failing to achieve participation in the blockchain.
The “timejacking” attack is similar. A hacker can theoretically alter the time handling of a node and tricks that node into operating on a temporary fork of the blockchain, often using multiple peers that are compromised to use their alternative fork for the attack.
Other attacks involve misdirection. The “selfish miner” attack was first theorized in 2013. It involves strategic timing with mining and adding the mined block to the chain, such that it essentially forks the protocol and forces other miners to waste their time and lose out on the benefits of mining.
A “partition attack” is a kind of attack where attackers segment the network, dividing it into several different partitions that cannot communicate between one another. Selectively blocking traffic essentially forks the blockchain, requiring consensus only within the partition. Similar attacks, called delay attacks, tamper with the speed that nodes can propagate their messages across the network.
One of the most common sorts of attacks is called a double-spending attack. With blockchain-based currencies, the network needs to agree that the request matches its ledger to verify a transaction. Getting all nodes on the network to agree takes time, though, and that lapse in time can be exploited. There are several kinds of double-spending attacks, including Finney attacks, Race attacks, and Vector76.
Denial of Service Attacks
One of the common threats to online businesses and services is the distributed denial of service or DDoS attacks. A DDoS attack involves thousands to millions of machines operating to send data to a server, far more than it can process, bringing it down. This happens hundreds of times every year, to everything from small businesses to major websites.
The distributed nature of the blockchain means it’s less susceptible to these attacks, but botnets can be very, very large, and can be tuned to attack multiple parts of a blockchain network at once. Additionally, numerous instances in the past have shown that even if the blockchain itself isn’t vulnerable, the hubs that use it are; coin exchanges are a popular target for DDoS attacks.
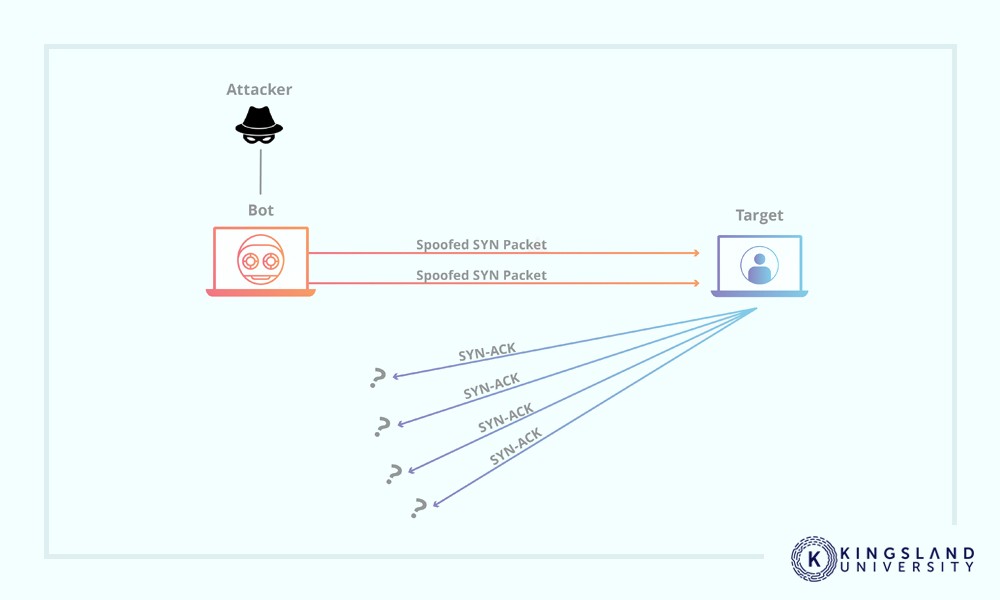
Additionally, many of the more common attacks, such as attacking passwords with dictionary brute-forcing, or phishing and social engineering users for their private information, can work to secure accounts on exchanges and other blockchain-adjacent technologies and platforms.
The very nature of the cryptographic protocol used in the blockchain can leave it vulnerable. Bitcoin is a prime example, using the ECDSA algorithm to generate private keys. Due to the size of the blockchain ledger, it appears that the algorithm used doesn’t have sufficient entropy and can generate the same key more than once. The hashing function used at the core of a blockchain needs to be appropriately complex and entropic to ensure security, and it can be difficult to foresee issues of scale.
On top of all of that, physical attacks can still work as well. One method for storing cryptocurrency “safely” is the Cold Wallet, a wallet storing the data completely segregated from the internet, out of the reach of digital hackers. Someone with the right access to the right facility, though, can simply steal a hard drive and all of the wallets it contains.
Novel Solutions to Novel Problems
Blockchain technology is new and interesting, and as such, thousands of tech startups and hundreds of established companies are working in the space. It’s ripe for innovation and experimentation, but that always opens up room for new attacks. All it takes is forgetting a key element of security along the way to leave a vulnerability open in new technology.
One of the most interesting uses of blockchain technology involves divorcing it from the cryptocurrency aspect of the tech and using the core blockchain protocol in other ways. This has fascinating potential and requires a lot of critical thinking and testing to spot potential security issues in the implementation of new technology.
Many of the problems we have listed up above have solutions, either in theoretical space or in actual implementation. Consider the problems presented and think about potential solutions. What might you come up with?
If the thought exercise interests you, and blockchain technology is something you find fascinating, you might consider pursuing a program to learn the ins and outs of the technology and its security challenges. Our program can certify you as a blockchain developer and prepare you to work in the fast-paced world of emerging technologies.
Whether you’re interested in developing blockchain technology for the next step in its evolution, or you’re more interested in the cat-and-mouse game of hacker versus cybersecurity expert, there’s room for you in the blockchain space. Learn the ins and outs of the technology today, and get started with your contribution to the technology tomorrow.


