
Any time you’re invited to a job interview, you need to be prepared for the questions you’re going to be asked. Interviews test personality, cultural perspective, and knowledge, so that managers can try to understand the candidate’s skills and abilities, as well as how they would fit in with the team.
While we can’t necessarily produce a one-size-fits-all guide to portraying yourself and your personality in an interview, we can help you out with the technical portion of the interview.
In many cases, a job interview in cybersecurity will have two phases. For one phase, you’ll take a practical skills test. A variety of businesses offer online skills tests for most CS career paths, including cybersecurity. You’ll learn everything you need to know to pass those tests in our cybersecurity program.
The other phase is the in-person (or online, or video) interview. Your interviewers will ask you questions about various aspects of cybersecurity, and it’s your job to answer them. Generally, your skills should be enough to help you pass, but it helps to be prepared. To that end, here’s a list of some of the most common questions you’ll encounter in an interview, and how to answer them.
What Is on Your Home Network?

Newcomers to cybersecurity often use their home networks as a testing ground for new technology and security measures. Discussing your home network architecture can show your prospective employer how seriously you take security. If you’re not willing to secure your home network, how can they trust you to secure a network that is orders of magnitude larger and more valuable?
What’s the Difference Between a Risk, a Vulnerability, and a Threat?
Different terms mean different things in a cybersecurity environment. Being able to explain and articulate the differences between each term shows you have a solid understanding of what they mean in a security context. To put it simply:
- A vulnerability is a weakness or flaw in a system that can be exploited.
- A risk is a vulnerability that has been discovered and flagged to be addressed.
- A threat is someone or something (hacker, virus) that is targeting a vulnerability.
You may also be asked to follow up on which of these is most important to address and focus on first. The answer may vary from organization to organization, depending on how proactive their security is.
What Is the Principle of Least Privilege?

Also known as the principle of least authority or the principle of minimal privilege, this principle is a way of thinking and securing a network that gives each process (or module) the bare minimum access and privileges on the network necessary to do its job, and no more. The less access any given module or person has, the less it can inadvertently mess up, and the less damage it can do if it is compromised.
Do You Believe That DNS Monitoring Is Important?
There’s not necessarily a right answer to this question. Some organizations believe that as long as DNS is functioning properly, it doesn’t need to be monitored. Others recognize that DNS monitoring can identify signs of a security breach since audits and logging can show malicious domains, denial of service attacks, and other threats. As a new grad and job seeker, you will likely want to err on the side of caution and answer yes, that monitoring is always important.
What Port Does Ping Use?
This, and questions like it, are traps. Ping is a function of a layer-3 protocol; ports are part of a layer-4 protocol. Ping doesn’t use ports in the same sense, so if you try to answer this as a serious question, you’re wrong. This is essentially a simple question used to weed out people who don’t quite understand how internet architecture and layers work.
What’s the Difference Between IDS and IPS?
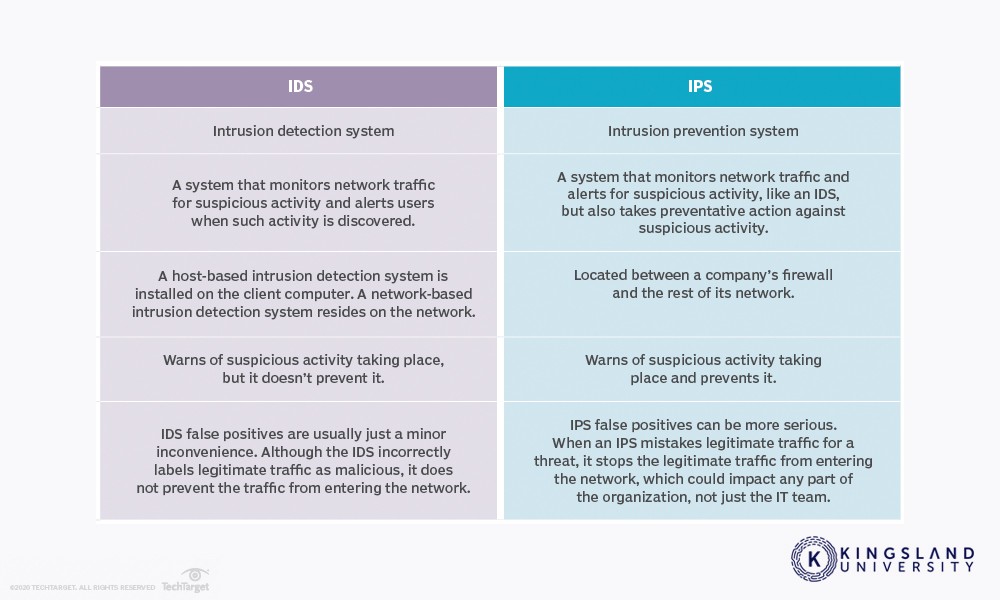
IDS is an intrusion detection system. It’s a monitoring system that does not take action on its own and requires human oversight to identify problems and interpret logs. IPS is an intrusion prevention system. It’s a control system used to prevent intrusions, like how an antivirus program catches and prevents malicious software from acting. Your interviewer is likely looking for an answer discussing the differences between monitoring and prevention.
What Is the Difference Between Hashing and Encryption?
This, and other questions like it, are an opportunity to discuss encryption in depth. Proper encryption is a large part of what cybersecurity experts manage. You can use this opportunity to discuss different kinds of encryption, like symmetric versus asymmetric, different algorithms, and other kinds of data protection.
For this question specifically, remember that encrypted data is converted from readable into unreadable data using encryption keys, and can be converted back into readable data if those keys are available. Hashing converts data into an unreadable format that cannot be reversed (barring a compromised hash algorithm).
What Signs Would You Look for to Identify a Compromised System?
A huge part of daily life for a cybersecurity employee is looking for, monitoring, and preventing compromised systems. Many attacks, both guided hacking and unguided malware, operate relatively silently in the background. It’s not like the movies, with flashing alarms and sirens. Malware doesn’t want to be detected, because it wants to act in the background.
Detecting compromised systems can be done in many ways, and we’ll teach you many of them. Knowing several methods for detecting compromised systems (such as DNS monitoring, above) will help you explain how you would monitor and identify a compromised system.
What Would You Do to Defend Against Cross-site Scripting?
Cross-site scripting, or XSS, is an injection attack on the client’s side. While defending against such attacks is partially a user-side problem, your organization can take steps to proactively prevent such attacks from happening. There are many options, including sanitizing HTML code, encoding special characters, and using anti-XSS tools. You may have your preferred methods, but the point of the question is to recognize that even though the attack is user-side, you can take preventative action.
Is the Cloud Secure? How Would You Secure the Cloud?
Cloud services put some of the onus of security on the cloud provider to keep their architecture up to date and keep monitoring and other services in place to ensure their infrastructure is not compromised. However, the applications you run and the data you store needs to be secured on your end as well. The cloud itself is not inherently secure – it’s important to acknowledge your responsibility for your organization – but it does limit the actions you can take to maintain security. Talk about strong authentication and passwords, encrypted traffic, and secure data storage.
What is the Difference Between UDP and TCP?
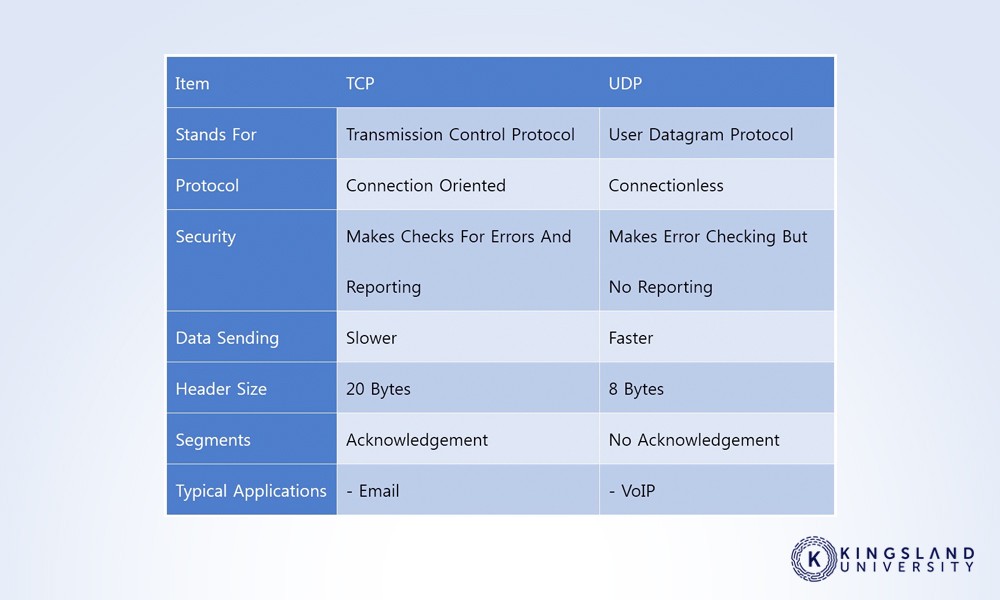
This, and questions like it, are basic questions meant to make sure you know how the internet works on a foundational level. In this case, TCP and UDP are both protocols for sending data back and forth between two devices. UDP is faster but has no error checking, while TCP numbers packets to ensure that data isn’t lost along the way.
What Tech or Security Blogs Do You Follow?
Cybersecurity is a constantly-evolving industry. It’s an arms race between companies and organizations defending themselves, and malicious actors trying to break those systems. As a cybersecurity expert, you are expected to keep on top of changes in the industry, including new and emerging threats. You will likely want to mention a handful of blogs, as well as individuals on Twitter you follow who post about the industry. It doesn’t necessarily matter which ones you list, but you want several entries on that list.
What Is the Biggest Threat Our Organization Faces?
There are a lot of different threats in the cybersecurity space, ranging from roving malware and bots to targeted phishing attacks. Monitoring the top threats is important. It’s also important to recognize the size and importance of the organization; a small company might worry most about generalized attacks, while a larger company might worry about targeted spear-phishing and state-sponsored attacks.
What Is Security Through Obscurity, and Is It Sufficient?

Security through obscurity is the concept that a system is secure because no one knows it exists. If no one knows about a system, they can’t target it for an attack. The trouble is, any system that is attached to the internet can be found, either through tracing traffic or through brute forcing connections. It’s similar to how your phone number can receive spam calls even when you haven’t published it anywhere; there are a finite number of phone numbers, so an auto-dialer can simply go through them one by one looking for a response. A system is never secure simply because it’s not announced.
What’s the Difference Between a Firewall and an Antivirus?
An antivirus is a control program that scans active processes and passive files looking for code that matches snippets in its database, to identify, prevent, and quarantine malicious code from being executed. A firewall is a device or control program that monitors and filters traffic, to protect an isolated network from external threats.
How Would You Prevent a Brute Force Attack?
Brute force attacks are usually targeted at login interfaces and simply spam login attempts using variations on common usernames and passwords, in an attempt to guess credentials that work. They’re easy to prevent, but steps do need to be taken to do so. Using complex passwords (and recognizing that dictionary attacks make length alone inadequate), limiting login attempts, and setting two-factor authentication are all important parts of this answer.
What Is the Difference Between White, Gray, and Black Hat Hackers?
Black hat hackers are malicious actors that attempt to compromise systems for their personal profit, usually to damage a company or to sell personal data. White hat hackers are ethical hackers, using hacking tools and techniques to demonstrate flaws in a system but leaving those systems alone, and informing companies about how to fix vulnerabilities. Gray hat hackers are white hat hackers who may use unethical actions to force results, such as trashing a system to prove a point.
What Is Phishing? How Can You Prevent Phishing Attacks?
Phishing is pretending to be someone in order to get a response. Sending an email to the organization pretending to be the CEO and asking for gift cards is a common scam. Phishing can be prevented in a variety of ways, including organizational policies that prevent sending personal information or gift cards over email, and email filtering that prevents credential mismatches (such as the CEO’s name attached to an email that isn’t part of your organizational structure).
How Would You Protect Against a DDoS Attack?
DDoS attacks are some of the most common threats online. Preventing them requires having a strong network with strong security, filtering packets, auditing traffic, recognizing the signs of an attack, and potentially using a service such as Cloudflare to prevent the attacks from reaching your servers.
What Certificates Do You Have?
There are dozens of certificates from half a dozen different certificate authorities. Our program prepares you to earn the Certified Ethical Hacker certificate and the CompTIA Security+ certificate, which you should test for and earn before applying for jobs. You may also want to explore and earn other certificates related to your intended career path.
Do You Have Any Questions?
This is usually among the last questions asked in an interview, and it’s another trap. Interviewers are looking for two things.
- First, they’re looking to see whether or not you have any questions at all. If you have none, chances are that your interviewer will cross you off their list. You’re not showing ambition or curiosity, which are important for any job. Always have some kind of questions prepared, so you can ask something relevant. Consider asking about any threats the company has faced in the past, and how they handled those threats, what security appliances they use if any, and what their biggest concerns are.
- Second, the interviewer is looking for the kinds of questions you ask. Specifics about the job are good. Generalized questions about the company can also be good, though if it’s public information that you should have looked up first, it can be a point against you. Avoid questions that could come off as smug such as “when do I start?”, which could come off as arrogant could potentially remove you from the candidate pool.
Research the company thoroughly before you attend your interview, and write down some questions you have to bring up after your interview has concluded.


