
Cybersecurity is an incredibly interesting field. Data breaches happen every day, from viruses to individual hackers to hacking consortiums looking to make money. The people on the front lines, fighting against these data breaches, live one of the most exciting and ever-changing lives in all of Information Technology.
People reach a career in cybersecurity through a variety of different paths. Some set out from the beginning aiming to become a security specialist. They go through college courses, get a degree, and move directly into the realm of security. Others start in different roles, like developers or engineers, and take an interest in security as they’re exposed to it. They take night courses, self-teach through online classes, and make their way laterally into a security role.
Still, others begin their careers from the other side, as hackers chasing bounties, and make connections in the security world as they do so. They learn how to protect a system by learning how to break it, and put together that knowledge and their experience into a career path.
If you have a keen interest in what protects a computer system from intrusion, how to break it, and how to harden it against attack, a career in cybersecurity might just be perfect for you.
Consider a Career Path
There are a variety of different career paths and specialties within the overall cybersecurity arena. You’re never locked into one role; experience and the ongoing development of your skills allow you to transition between them as your interests align.
Security Architect is a solutions engineer. Architects spend their time designing systems and hardening them against intrusion, implementing network security protocols, and designing the overall security flow for an organization. Architects tend to be in mid-to-high-level positions, managing security operations for an entire company or organization. They are responsible for managing firewalls, network security, operational security, and standards implementation. They’re also responsible for aggressive testing of their corporate networks, including penetration testing, phishing training, and risk analysis.
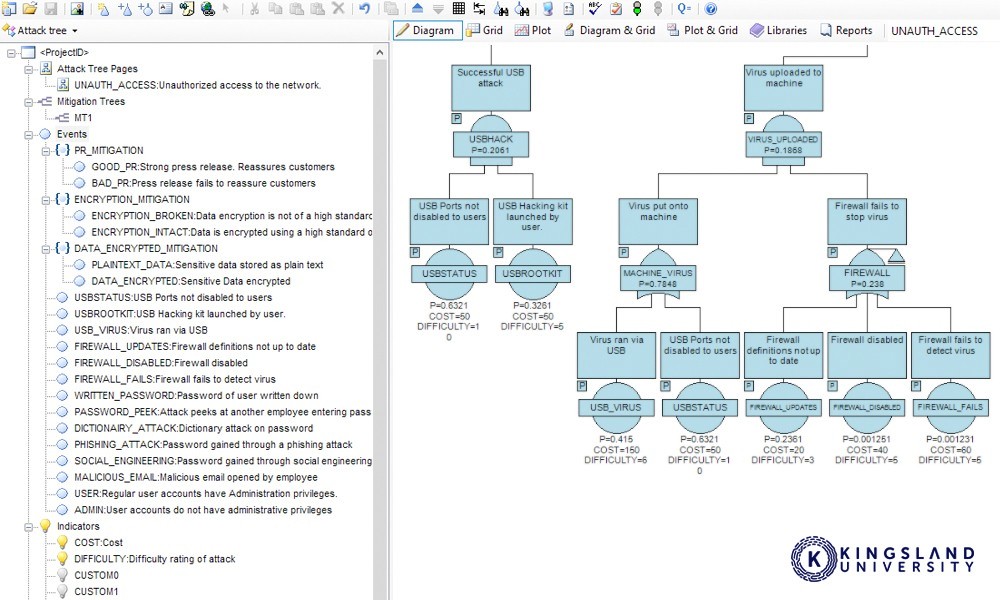
A security architect is an upper-level position, usually requiring 5-10 years of relevant experience in networking and security. Students looking to pursue this position would usually start as general Computer Science students with an emphasis on security, and follow a career path beginning as a security or systems administrator, and progress to security engineers as they gain experience.
Security Consultant is a role similar to an architect, with less focus on engineering solutions and more on exposing vulnerabilities. Consultants work for anyone who hires them, rarely sticking with a single organization for long.
The security consultant role is a natural progression for both students with a security interest who want to focus on pen-testing and vulnerability assessments, and for ethical hackers who want to legitimize their skills with an official role.
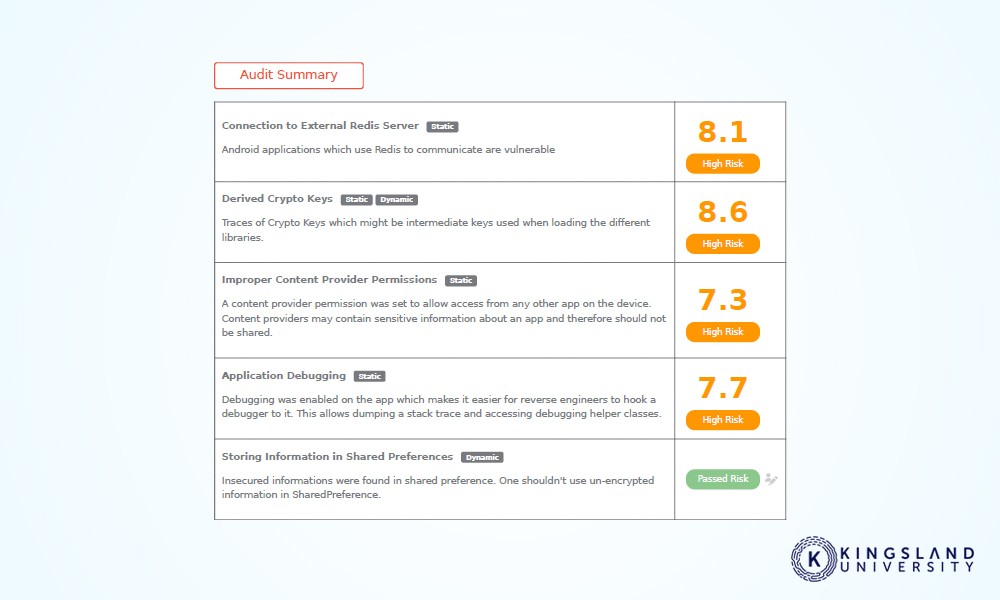
A security consultant either begins as a hacker or starts their career as a computer enthusiast with a focus on computer science and networking. Schooling progresses through general CS content and networking to security and certifications.
Penetration Testers are also consultants, working with any company or organization that hires them. They’re a “red team” force, operating as controlled opposition. A company hires a penetration tester to put its security to the test, and they do so, simulating real-life cyber attacks ranging from DDoS to phishing to the use of common NetSec tools.
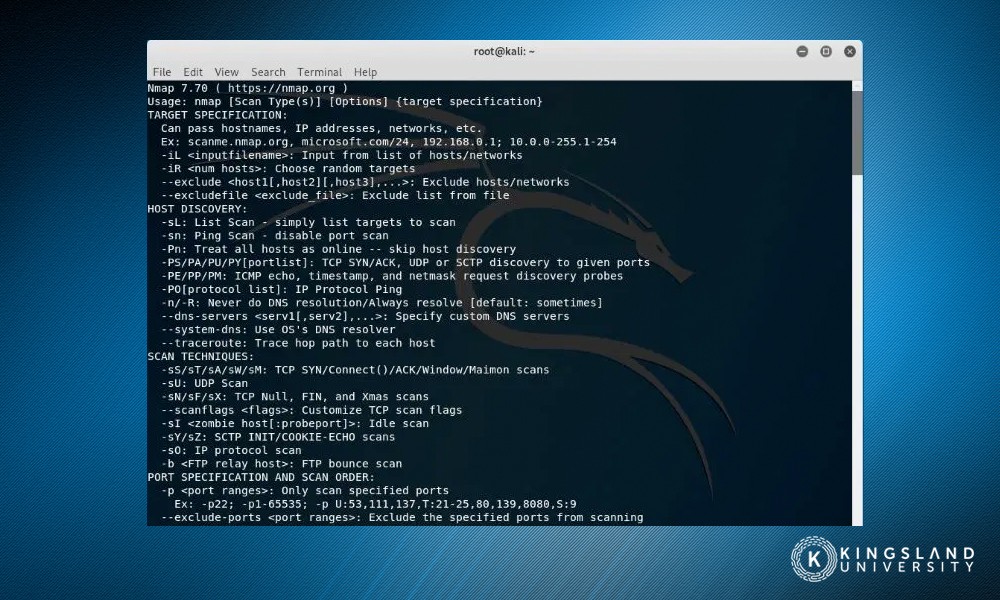
While many pen testers start life as ethical hackers, many more of them progress through certification processes and information technology education. In the past, a pen tester might spend time learning on their own, in the dark web, and hacking circles. Today, the educational path is more codified, and entire degrees and certifications can be found specifically focusing on pen-testing.
Where a security consultant identifies weaknesses in an organization’s security, then works with management to plan and implement upgrades to security, a penetration tester only handles the first part. They generate reports for the vulnerabilities they find, discuss solutions with management, then move on to their next client. It’s up to the organization to follow their advice.
Chief Information Security Officers are the top dogs of the cybersecurity world. They’re the C-level executives who have spent at least a decade working in security, learning all there is to know about information security and the threats an organization can face. The average CISO has spent 6-12 years working in cybersecurity before reaching their role. They also frequently continue schooling for a Masters in Business Administration, along with any relevance networking and security certifications they can find.
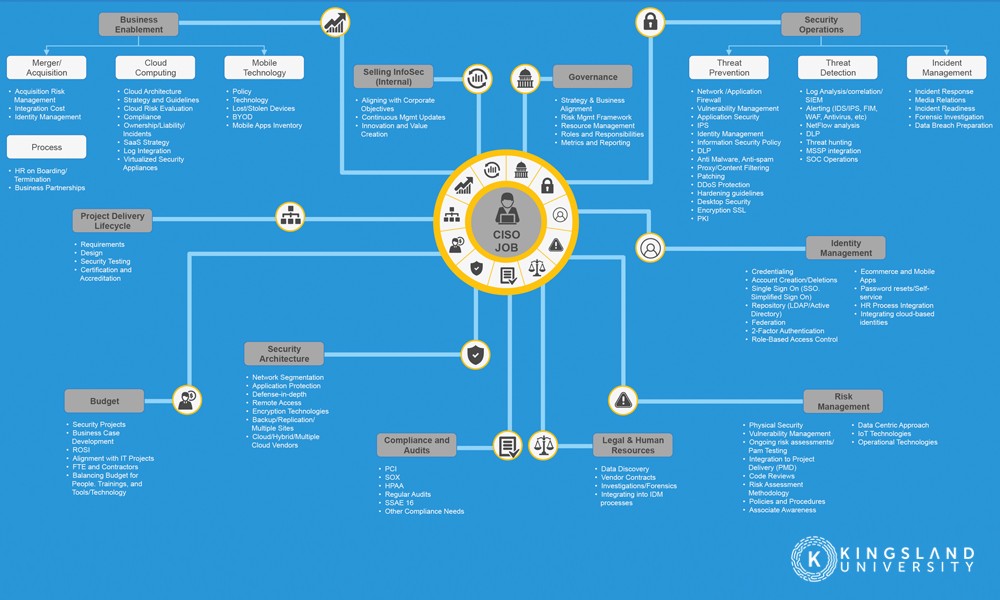
If you’re interested in cybersecurity, regardless of your eventual career path, you need to establish a baseline level of education in information technology, networking, systems architecture, and security protocols. A good cybersecurity program covers a variety of bases.
Here’s what you should learn.
Cybersecurity and Cryptography Fundamentals
Among the first things a cybersecurity student should learn are the fundamentals of cybersecurity itself. The flow of data, how data is handled, how networks work, and encryption.
Encryption is especially important. How it works, how it can be broken, how it can be mishandled and misused, and in what ways it should not be trusted, are all important pieces of knowledge for a cybersecurity expert.
This overview should consider typical network structures and security protocols, their vulnerabilities, the attacks that are commonly used against them, and how they can be hardened against those attacks. Everything from the basic use of firewalls to complex syntax analysis to identify common phishing techniques might be covered in this realm.
Cryptography gets technical, into how encryption works, how stronger bit encryption is harder to break, how public vs private key encryption works, the differences between symmetric and asymmetric encryption, and the risk encryption faces in the modern technology landscape.
Network Administration, Architecture, and Scripting
Every good cybersecurity engineer needs to have a working understanding of networks. How networks are put together, how network protocols work, how communications happen between networks; it’s all foundational to the internet itself. Understanding how networks are made allows you to understand how they can be broken, overwhelmed, or exploited, and likewise how they can be hardened and improved.
Alongside this comes scripting. A large part of many cyber-threats is scripted attacks, that are not very sophisticated but make up for it in sheer volume. Learning scripting for both system administration and understanding attacks allows you to develop a working knowledge of both network administration and pen-testing.
A course on networking and network administration also opens up doors as a network admin, which works well as an entry-level position before pivoting with more hands-on experience towards network security. This is also where many students choose to pursue a particular path within cybersecurity, such as network security or information security.
Defensive Security
Defensive security is the realm of the security analyst, the CISO, and everyone in between. A company or organization must defend itself from threats, domestic and abroad, large and small. Understanding those threats, and how to deal with them, is a core part of any cybersecurity specialist’s arsenal.
Defensive security will cover a variety of bases. It covers things like institutional policy and compliance, such as how emails and data are handled, how access to the network is allowed, and how company devices are tracked and secured. It includes an overview of enterprise-level security architecture, which is how the largest companies and organizations secure their networks, the high-level devices and appliances that can make it happen, and the software solutions you need to know.
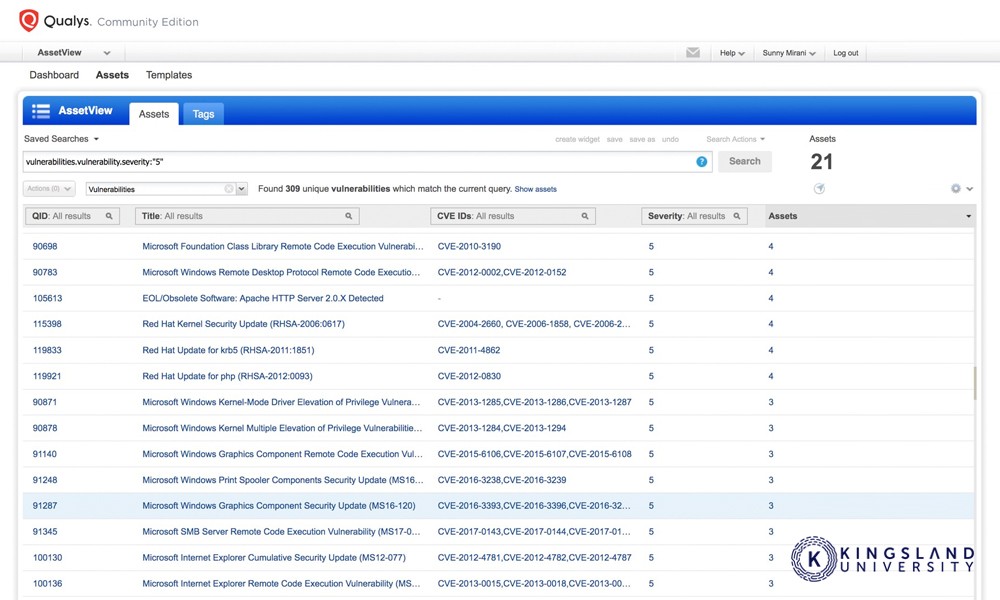
An overview of defensive security will also include an auditing process, and the tools necessary to analyze the results of an audit to spot red flags, vulnerabilities, and violations of policy. This is an inside-out approach to security: identifying flaws from the inside, to address them before they’re attacked.
Offensive Security
Offensive security is the realm of the pen tester and the red team. It takes information from network architecture, company policies, and security systems, and twists it. How does one assault and break these fortifications? How do you identify the security an organization is running, and what vulnerabilities should you look for?
The arena of offensive security is the arena of an ethical hacker. Learning how to penetrate systems, and then do no damage, but rather document and report those vulnerabilities to the organization in question. This can be lucrative as a career path, either chasing bug bounties or working as a penetration testing consultant company.
Threat Analysis and Prevention
Once the foundational knowledge is in place, it’s time to bring it all together. The capstone of a cybersecurity course is building upon the theoretical knowledge to develop hands-on awareness of threat vectors. Learning to recognize and analyze threats, both potential and active, as well as the signs of past intrusion. This section includes threat modeling, theoretical threats, and active pen testing and defense against it.
In particular, this segment needs to cover an incident response. When an intrusion is detected, what happens? What do you do immediately, what do you do the next day, and how do you follow up on the incident? Learning how to analyze a threat to identify data loss or damage to systems, writing incident reports, and reactive hardening to prevent the same intrusion from happening again are all important skills.
Example Certifications
There are a variety of certifications that have been developed over the last decade or two, designed to demonstrate your knowledge and skill in different security areas. Here are some of the more common certifications you’ll want to investigate and prepare for.
CISSP: Certified Information Systems Security Professional – This certification is provided by ISC2. It’s aimed at certifying security knowledge for those looking for high-level roles in cybersecurity, including CISO, Director of Security, and Security Systems Engineer. It also meets the criteria to be a Department of Defense certification and is appropriate for those looking for a governmental security role.
ISC2 provides several other cybersecurity certificates, aimed at other roles in the security field. These include the SSCP security administration certificate, CCSP cloud security certificate, CAP security assessment, CSSLP secure software developer certificate, and HCISPP healthcare security certificate.
CEH: Certified Ethical Hacker – Provided by the EC Council. It’s a course and certification test that teaches students the tools and processes necessary to hack a company lawfully. Its certificates are designed and aimed at a penetration tester or offensive security expert, and it’s kept up to date with new and emerging attack vectors so it’s always relevant. A large part of modern cybersecurity courses is aimed at preparing students to earn this certificate.

Students who earn the CEH certificate have the knowledge and experience necessary to thrive in a wide variety of security roles, including pen tester, security analyst, vulnerability assessor, infosec administrator, and cybersecurity auditor.
SANS: Systems Administration and Network Security – The SANS institute provides courses and certification for a wide range of systems administration and security roles, with knowledge specialties at all levels. They offer courses and training, as well as certification tests, and allow both self-guided and in-person courses. Through their organization, a student can take specific courses to earn certifications to enhance their career prospects or pursue an entire Masters Degree (and everything in between).
Security+ – Provided by CompTIA, the Security+ certificate is one of the more common and broadly-recognized cybersecurity certificates in the IT world. It’s a test that emphasizes hands-on skills, so any employer who sees it knows that the certificate holder knows their stuff.

It’s excellent for an entry-level cybersecurity graduate, as an accompaniment to an information technology degree or computer science degree, or as a stand-alone test to progress the overall career path of a cybersecurity worker.
Kingsland University Cybersecurity Program – The Kingsland University Cybersecurity Program is a complete online course from an accredited education provider that helps its students learn and understand the fundamentals, as well as more advanced skillsets like penetration testing and network security. It also has an exam prep stage to help students pass the CEH and Security+ certifications listed above. This is ideal for new students who aren’t already heavily educated with cybersecurity fundamentals.
The career of a cybersecurity expert is an interesting one. It’s a very sophisticated career path, with a mixture of understanding the foundational technologies of the internet and the cutting-edge vectors for threat and response. If this ever-changing, ever-challenging role sounds like fun, it’s a great career path for you.


