
Cybersecurity is a growing industry. As more and more of the world does business online, with interconnected devices and networks performing virtually any task, the need to secure those processes and networks is increasing. Global cybersecurity spending is set to exceed a trillion dollars, and the demand for cybersecurity professionals is on the rise.
When it comes to securing a business, there’s more to it than just changing passwords on a regular basis and making sure your network has a firewall. Whether you’re a business owner looking to secure your company, or a student looking to become the cybersecurity expert for a business, you’re going to want to know how to implement modern cybersecurity practices. Here are eight things you’ll need to do.
1. Institute OpSec Processes
OpSec stands for operational security, and it’s the term that encompasses all of the individual business processes that put security first. It consists of a five-step process.
- Identifying Sensitive Data. This can be business or trade secrets, intellectual property, customer information, employee information, and more. You need to know what you’re protecting so you can figure out how to protect it.
- Identify Possible Threats. What threats and threat vectors should you be aware of? Are you looking to protect against disgruntled employees, outside hackers, determined opposition, nation-state actors, impersonal viruses, or what?
- Analyze Existing Security. You need to know where you are so you can determine how to get where you’re going. Every line from A to B needs to know what A is.
- Appraise Risk. For each threat vector, determine the level of risk associated with it, and the damage a breach could do.
- Establish Countermeasures. With everything above determined, you can enact procedures, implement technology, and harden vectors against intrusion.
This is the basis of security in the military, and it’s increasingly being adopted as a general framework for security in the civilian sectors as well. Putting this process into action requires knowledge, a framework, and the authority to implement the procedures that need implementing. It also requires institutional buy-in, meaning you as a cybersecurity expert must be able to argue the importance of each step of the process.
2. Practice the Principle of Least Privilege
The POLP, or Principle of Least Privilege, is an operational security measure that just about every dedicated cybersecurity specialist should know and implement to the best of their ability.
The principle is this: Every user, every module, every app, every API, anything that interfaces with any part of your network, should have at MOST the access absolutely necessary to do its job. A user doesn’t need Admin access on their laptop to perform their daily tasks. An app doesn’t need full database access when all it needs is read-only to lookup data. A secretary doesn’t need Admin access to their boss’s computer, only access to things like scheduling and calendar apps. And so on.
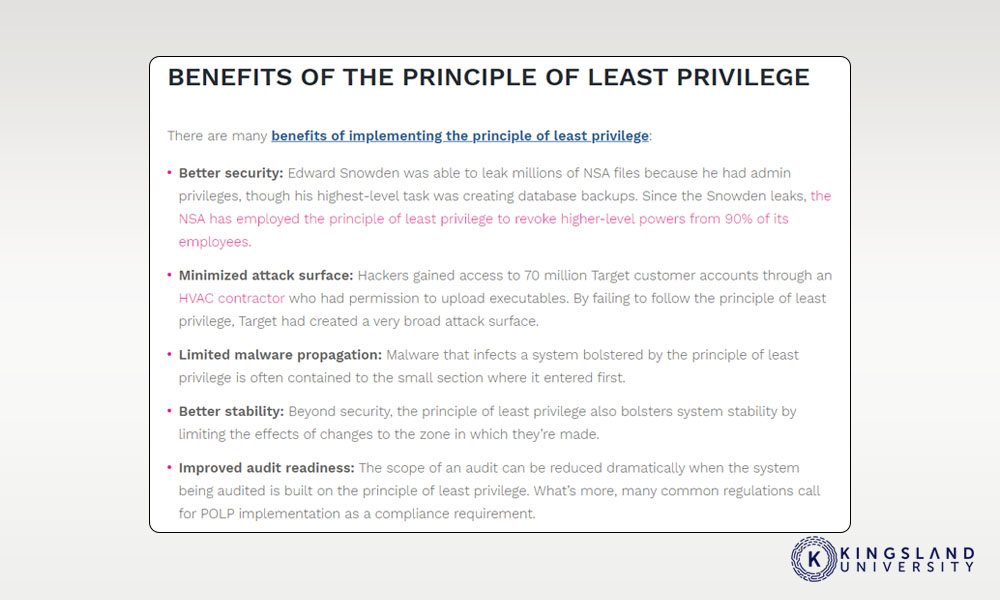
The idea is all about segmentation. If any app is breached, it only has access and power to do a limited amount of damage or recover a limited amount of data. The less access any one module or any one user has, the less can go wrong if that asset is compromised.
Consider common threat vectors. If an employee opens an email that contains a virus, what can get infected? Will their laptop potentially get locked and require a wipe? Will their access crypto-lock an entire network share? Or do they have full access to the network, grinding your entire business to a halt? How long will this take to recover from? Do you have remote backups you can use for a restore, or were your backups on the same server and thus inaccessible as well?
3. Build Awareness of Phishing Techniques
Phishing is one of the most common methods of compromise for any business. A malicious actor can spoof the email header for an email such that it looks like it’s coming from an internal source, whether it’s a coworker, a boss, or a C-level executive. A user who doesn’t look deeper might be convinced to take a malicious action, such as buying gift cards to send to the scammer using company funds, giving out user information to an admin account, or simply opening a file that contains malicious code that then crypto-locks the network.
Phishing training requires teaching your employees about how phishing works and how to spot those attempts. It may also require securing your email system against external messages and flagging messages from external sources with a visible banner that helps warn users if one slips through. No technical solution will catch 100% of phishing attempts, just as training cannot prevent everything. Thus, you also need a recovery plan in the case of a breach.
There are services that can help with this. Some services create phishing emails and send them to your organization, to see who bites and generate a report. This can go well, or it can go poorly, as the recent GoDaddy phishing training drama has shown.
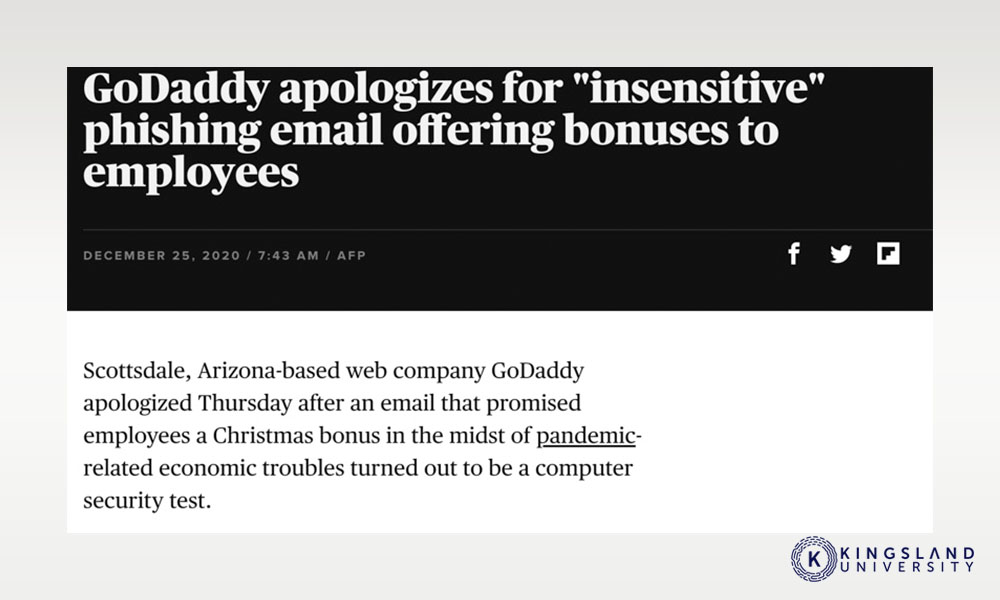
Regardless, building awareness and good email hygiene is a critical part of securing your business network.
4. Create a Security-First Onboarding Process
Many companies fail to have a modern security process in place. Thus, when a new employee joins the team, they may be used to business processes and casual actions that place the company at risk, often without realizing the risk inherent in what they’re doing.
A good company managed by a cybersecurity specialist needs to have a robust onboarding process that keeps security in mind. This process may involve many steps, such as:
- Determining the department and role of the new employee, and thus what access they need for their job.
- Determining any special access or needs the employee will require as part of their role.
- Establishing a workflow for approval if the employee needs greater access, temporarily or permanently. Who do they contact, and who needs to approve it?
- Creating a generalized approval process for the creation of new user accounts.
- Creating and provisioning any physical hardware the user may need, such as their laptop, a 2FA fob, physical access keys, and so on.
- Providing an onboarding document with established security procedures and measures the employee will need to adhere to.
This onboarding process should be streamlined so as not to overwhelm the new employee with strict security measures, while also ensuring that they know and adhere to best practices. Over time, more and more businesses will implement these security measures and it won’t be as much of a change for many new employees, but until that time comes, an onboarding process will be critically important.
5. Keep Up with Ongoing Security Training
Cybersecurity is one of the fastest-moving fields in the world. It’s literal warfare, an arms race between malicious actors and defenders. Often times, your company won’t be anywhere near the front lines, the constant battleground between governmental agencies. Attack vectors slip, however, and eventually, malicious actors get ahold of threats they can use against targets less likely to be hardened against them.
As a cybersecurity expert, your job is to stay up to date with the world of security. That means following key Twitter accounts, reading security blogs on a daily basis, and continually learning about new threats and new means of defense against them.
Moreover, you are responsible for implementing new security measures as they affect your infrastructure. If you use a particular platform or app, you need to be aware of new threats to those surfaces, and how to harden your own surface against them.
This may mean implementing new hardware or new software. It may mean scheduling unplanned critical maintenance windows to push security updates. It may mean manually changing files or configuration to remove threat vectors.
It may also mean implementing new training procedures for your organization. Occasionally, new threats require institutional buy-in to avoid, and your security will only be as good as the training your employees receive. This is one of the most difficult challenges a cybersecurity expert faces, and it’s one you’ll need to navigate.
6. Implement Network Security Processes
Overall network security is complex and as varied as the organizations that have networks. Every junction between apps, every public-facing user account, every accessible port, is a potential means of attack. Thus, you will be responsible for implementing network security.
Network security is in part made up of user training. Ensuring that users know how and when to access a network, how to keep their own devices secure and/or off of the company networks, and making sure your internal networks are still hardened in the event of intrusion are all important factors.
You may also be responsible for buying, configuring, and implementing security appliances. Hardware firewalls, air gaps, and other physical means of security can be important for securing a company.
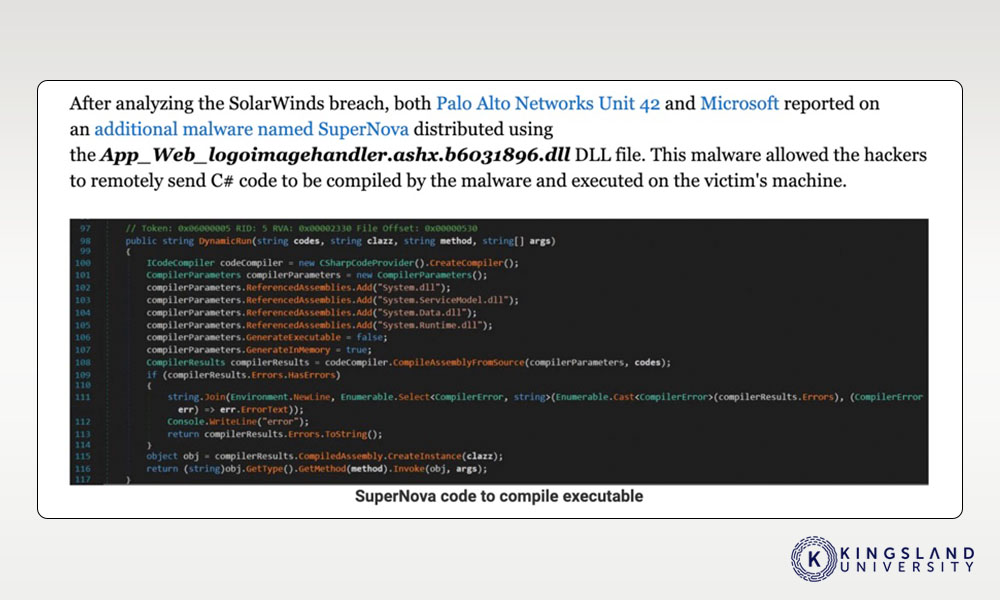
It’s worth remembering that even the most secure network is still vulnerable to novel vectors. Supply chain attacks, for example, can install backdoors or malware into systems before those systems are even built, such as in the recent SolarWinds attack. This is even more reason to stay up to date with security, to ensure that you know of any such attacks before they become active threats to your organization, and you can take action to mitigate any damage they might cause.
7. Install Passive and Active Intrusion Detection
There are two ways to handle active security monitoring. One is through an automated, passive intrusion detection system. Passive systems are similar to an antivirus; they scan through logs, configuration files, and system files looking for signs that modifications have been made. In order to operate, these systems require definitions; hashes they can use and files they can compare.
The pitfall of these systems is that they’re static. If a malicious actor understands how they work, they can develop malware that circumvents them, subverts them, or avoids them. If you have a security camera watching the front door, and a criminal knows about it, they can use a side door instead. If you have cameras on every door, they can use the windows. A passive detection system is only as robust as its definitions, and it can’t watch everything all the time.
This is why passive systems need to be augmented with active, usually human, monitoring. Looking for strange occurrences, odd patterns, and potential signs of intrusion is a large part of the day-to-day job of a cybersecurity specialist.

One thing that it’s important to recognize is that active malicious threats, much like home invaders in physical space, tend to go for targets with the least resistance. Even many automated security threats start by detecting active monitoring, and simply don’t execute if there’s a chance they’ll be spotted right away. This is part of how the SolarWinds attack flew under the radar for so long; it only attacked systems that weren’t watching for an intrusion.
8. Pay to Train Employees in Advanced Cybersecurity
A final piece of advice for business owners specifically is to make sure you have a dedicated cybersecurity expert on staff. If you don’t have one, hire one. If you don’t want to hire one, consider paying for someone on your senior IT team to get certified in cybersecurity using an online program.

It pays to have someone on staff, rather than a consultant, handling your cybersecurity work. They can leverage more authority, have more familiarity with your systems and company culture, and will be better at detecting and preventing common threat vectors your company is susceptible to.
It’s also an option to combine both an internal and an external security company. Keep internal security staff on hand to do the architecture and monitoring. Hire an external company to run intrusion tests like phishing tests, Red Team attacks, and other forms of security auditing.
The key, of course, is empowerment. All the cybersecurity knowledge in the world can’t help your company if you’re not empowering the people in charge to make changes for the better. So, train your employees, empower them to make changes, and make your company a hard nut to crack.


