![]()
With every passing year, cybersecurity becomes more and more of a concern. The sophistication of threats that even the average internet user needs to be aware of is growing, and even that is eclipsed by the arms race happening on the business and governmental levels.
If you’re interested in the fast-paced world of cybersecurity, it helps to have a solid education. More than that, though, you need tools. Education lets you learn how and when to use what tool, but without the right tools, our jobs would be impossible.
Now, we’re not saying you need to familiarize yourself with everything on this list before you can take a course or proceed into a career. Many of these tools are things you’ll pick up as part of your job. It simply helps to have familiarity with what they are and what they do, so you have some idea of how to use them before you’re called to do so.
Network Hardening, Monitoring, and Security Tools
This first section of tools is a broad set of applications. Some of them aim at defensive security or monitoring your network traffic, while others specialize in active security by attempting to penetrate or sniff your own networks. They’re useful for both pen testers and cybersecurity specialists who need to secure a network from the inside, and who want an automated system capable of seeking out known vulnerabilities to address.
Argus – Argus is a comprehensive traffic monitoring tool that is open source and works for most network configurations with minimal hassle. It analyzes network packets and delivers traffic reports, and can become a great early warning system for network intrusion detection.
Packet Fence – Access control is the core of a good security policy. Packet-Fence is a robust, free solution for managing role-centric access control across networks of any size. It includes a variety of useful features, including BYOD support, segmentation, and malware removal.

Wireshark – One of the most popular packet sniffers and traffic monitors in the world. Wireshark is an industry-standard tool for monitoring, analyzing, decrypting, and logging network traffic. It’s extremely powerful in the right contexts and should be part of any cybersecurity expert’s toolbox.
Snort – Snort is an active traffic monitoring tool that works sort of like an antivirus for web traffic. It monitors traffic, including attempted traffic to ports and servers that indicates an attempt to penetrate a system from many other tools on this list. It’s an active defense tool, so you will want to learn how to configure it and how to read the logs it provides.
Splunk – Another common traffic analysis tool. Splunk is popular in the enterprise space and amongst small-scale security companies. It’s fast, versatile, and above all, user-friendly. It can also perform historical searches on network traffic logs to identify traces of threats in the past as well as current threats.
SpyCloud – While not an active tool for protecting your network, this is a scalable tool that crawls the less savory places on the internet looking for specific signs and signals that indicate your company’s data has been breached. Nothing is worse than finding organizational account information in a data dump and not knowing how it happened. This tool alerts you when this occurs, so you can take action to prevent that data from being used.
Breach Alarm – Similar to SpyCloud, Breach Alarm is an alarm system that alerts your organization when there are signs of a breach or intrusion. It primarily focuses on signs that passwords from your organization have been exposed.
NoMoreRansom – Ransomware attacks are some of the most common and most devastating attacks on the web for an organization that is not prepared. Abrupt encryption of your network and devices can cripple or destroy a company. In many cases, organizations are left with no choice but to pay a ransom. This site offers known decryption keys for older ransomware attacks and can save an organization millions on ransom and recovery processes.
Password Auditing Tools
Passwords are still the go-to means of authenticating users within software ecosystems, but they have a huge array of vulnerabilities, from known password lists to dictionary attacks to attacks on the infrastructure or encryption of the passwords themselves. Part of your job as a cybersecurity professional will be managing passwords throughout an organization, so knowing how to audit them for weaknesses, and minimize the threat of weak passwords in the user ecosystem, is critical.
John the Ripper – John is a password auditing, cracking, and general security tool. It can crack passwords through a wide range of security protocols, transmission methods, encryption protocols, and static locations. It can identify both weak passwords and weak authentication processes, to help secure an organization against typical login attacks.
KeePass – There are many password managers on the market, but none are as fully embedded in enterprise-level and business-grade life as KeePass. KeePass is a simple password manager, able to store a variety of complex, secure passwords for different elements of an organization while allowing the user to choose a more memorable password as a master password. It’s an indispensable security tool for defensive security and maintaining secure passwords.
Web Vulnerability Tools
The majority of cybersecurity threats come from one of three vectors: infected emails, infected devices, and malicious traffic. There are thousands upon thousands of malicious bots, actors, scripts, and services out there, constantly seeking out vulnerabilities in infrastructure. Security through obscurity is not possible. As such, using tools like these allows you to scan your network from the outside in, to seek out potential issues and vulnerabilities to address before someone else finds them and exploits them.
Nikto – Nikto is a web server scanner that comes pre-loaded with a wide range of tests it can run to scan a server for vulnerabilities from the web. It checks for everything from out of date software to known malicious or vulnerable files to version-specific problems in over 270 configurations.
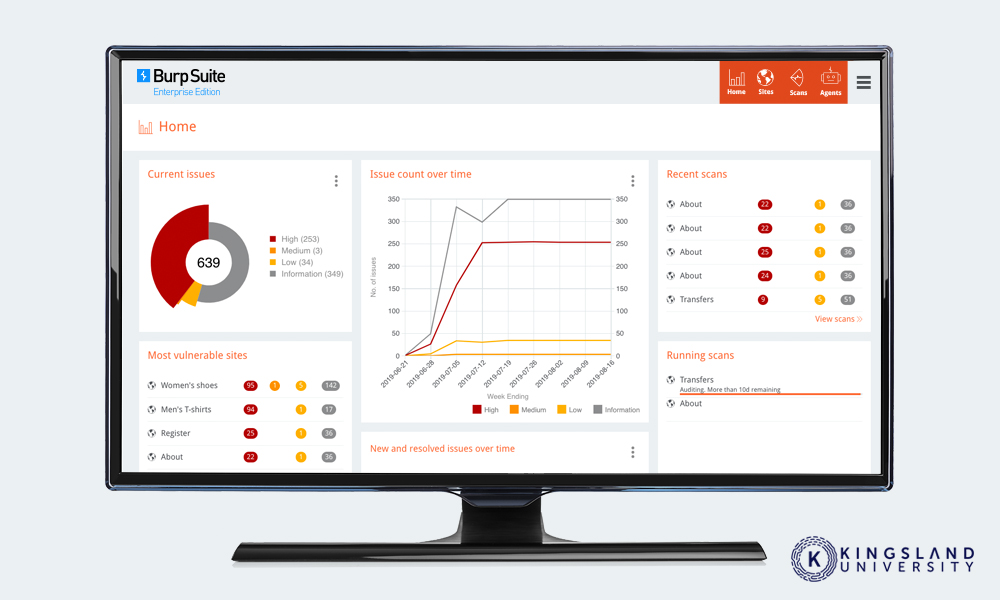
Burp Suite – Burp is a range of tools including a broad-spectrum web vulnerability scanner, scheduled scanner, and a suite of manual tools used to scan web traffic and web servers for vulnerabilities. It offers a free community-supported version, as well as both professional and enterprise versions with additional features and integrations with other cybersecurity tools.
Nessus Professional – Nessus is one of the most popular vulnerability assessment tools in corporate and enterprise space. It not only scans for issues but can fix them from where it sits if it has the access and authority to do so. It’s very common in professional cybersecurity, so learning how to use it is a good idea for any prospective student.
Acunetix – Acunetix looks at another surface vulnerable to threats that many of the others on this list do not. Checkout processes, shopping carts, login pages, and online forms all are interfaces where an attacker can submit data to a server to be processed. These are vulnerable to attacks such as SQL injections, which can compromise a server without ever setting a digital foot inside a network. Acunetix is a tool used to analyze and fix vulnerabilities in these processes.
Encryption Tools
There are malicious actors monitoring traffic, whether it’s wi-fi traffic or web traffic, looking for opportunities. The best way to avoid detection and keep from giving them those opportunities is to encrypt as much of your traffic and data as possible. Using end-to-end encryption, routing, and other forms of security is a step in the right direction.
Tor – The Onion Router is a service that anonymizes traffic and makes it difficult to trace the entry and exit points of web traffic. It’s useful both for penetration testing and for encrypting and anonymizing traffic, and while it has some drawbacks, it’s a good tool to learn how to use appropriately.
TCPCrypt – While end-to-end tunneling and full traffic encryption are important, sometimes you can’t immediately implement them. When you have no other option but still want to encrypt as much of your network traffic as you can, TCPCrypt does it. It automatically encrypts traffic whenever it can, and if the endpoint doesn’t support encryption, it falls back to TCP traffic gracefully.
Penetration Testing Tools
Sometimes, you’re not looking to play on the defensive. Many cybersecurity experts go on to be part of the “red team”, taking up the role of the ethical hacker, looking for vulnerabilities in an organization from the outside, and working with the company to fix those problems before a less ethical actor discovers them. These tools can be used defensively to secure your own network, or they can be used offensively, to bug hunt and ethically hack a network. They’re versatile and great to learn.
Aircrack – Aircrack is a complete suite of tools to analyze and attack wi-fi networks. It can monitor and packet capture wi-fi traffic, attempt a variety of common attacks, and test the security of a given wireless network. It’s a good tool for penetration testing, auditing, and protecting your network.
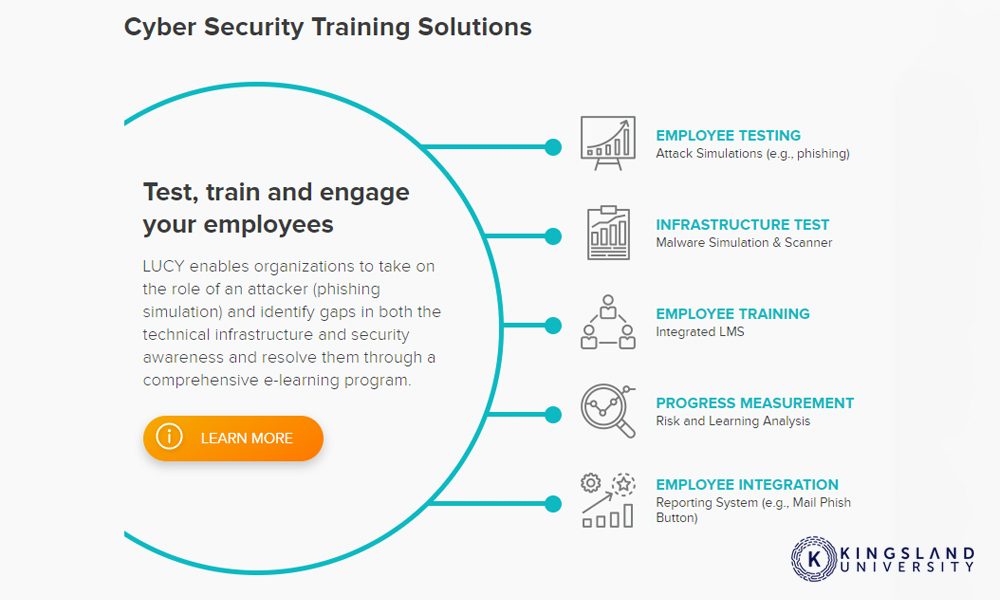
Lucy Security – One of the simplest attacks people fall for every day is the phishing email. A sufficiently convincing email can trick bored employees into all manner of vulnerable states, from sending money to an attacker to installing malicious code. Lucy is one of a range of tools aimed at protecting against email-based threat vectors, including phishing messages. It can also simulate phishing attacks against your organization, as part of email security and training procedures.
Metasploit – One of the world’s foremost pen-testing platforms and frameworks, Metasploit is an open-source platform with commercial support for organizations looking to attempt to compromise their own networks. It’s loaded with recent, common, and cutting-edge exploits, and can help an organization preemptively defend against attacks that aren’t coming yet.
Nmap – Nmap is among the simplest and most basic tools you’ll learn about as a cybersecurity student. It’s a simple tool designed to map out as much of a network as possible, including scanning for open ports, accessible services, and information about the devices attached to the network. It’s useful for penetration testing and for mapping a network you’re unfamiliar with, to look for potential vulnerabilities and unknown devices.
Platforms, Suites, and Resources
The modern security environment is filled with individual tools, but many security firms have grown tired of needing to accumulate and use dozens or hundreds of disparate tools. Instead, they offer suites of tools designed to work together, platforms with tools already installed, or suites of tools that help professionals do their job with a minimum amount of setup.
Kali Linux – We all know what Linux is, at least in the abstract, but a cybersecurity professional will need more intimate knowledge of the operating system. In particular, the Kali distro is pre-loaded with over 300 different tools for everything from network analysis to penetration testing to logging and more. Every cybersecurity pro should have a ready installation set up for when the need arises.
Got Phish – Run by the Twitter account SwiftOnSecurity, this web page is a list of resources for how to handle a phishing attempt that reaches your organization. Everything from evaluating the nature of the threat, to reporting it to relevant authorities, to dealing with attached malware, to blocking the threat is covered.
OpenVAS – The Open Vulnerability Assessment System, is an extremely robust platform used for scanning and assessing vulnerabilities in a network, from inside or out. It maintains a list of over 50,000 known vulnerabilities to look for and receives daily updates of new threats detected in the real world and by ethical hacker contributors.
This list is, of course, by no means comprehensive. There are hundreds of security tools out there, from the smallest of the pen-testing utilities to the largest of the enterprise platforms. It’s a good idea to review them, learn what they do, what sort of tools exist, and how they can be configured. With a broad, basic knowledge, you can leverage your cybersecurity training to utilize the tools specified by your organization, and bring new recommendations to your team when you’re hired.
Do you have any experience with the tools we’ve listed above? What are your thoughts? Be sure to let us know down in the comment section down below!


